NFS Ports
Network File System (NFS)
A networking protocol for distributed file sharing is called Network File System (NFS). In order to make a file system available to users of remote computers, Sun Microsystems created the Network File System in 1984. It enables users to read, save, update, and share folders or portions of a file system on a networked server.
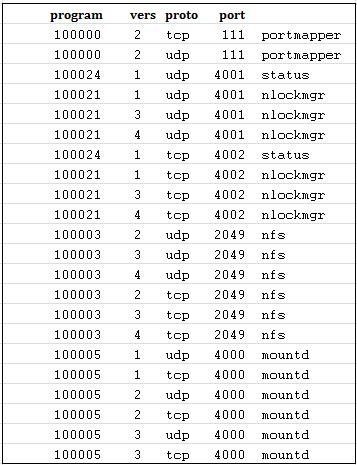
NFS ports
Default port 2049 is used by NFS. The portmapper service is used by NFSv3 and NFSv2 on either TCP or UDP port 111.
Port 111 (TCP and UDP) and 2049 (TCP and UDP) for the NFS server.
Moreover, there are ports for the NFS lock management, cluster and client status, and 1110 TCP and UDP respectively for the latter (Port 4045 TCP and UDP). Depending on the cross-gateway services required, only you can decide which ports you need to open.
Some vendors also support a version of NFS based on Secure RPC, which addresses many of the problems with authentication, providing better authentication both of the client machine and of the user. Secure RPC has several problems that also apply to NFS implemented on top of it:
- It is not widely supported; it is available almost exclusively on Suns.
- The process of exchanging keys between machines is difficult.
- It doesn’t perform as well as standard RPC. (NFS is particularly performance-sensitive.) The sizes of the public keys are too small docstore.
NFS Authentication
NFS was originally designed to be used within local networks for file sharing, and although it can be tuned to work over a network that has delays, it is unsafe to allow across a firewall for various reasons. NFS’s main security problems are:
- The NFS server relies on the IP address to authenticate client hosts, making it vulnerable to address forgery.
- The NFS server relies on the client to authenticate the user, making it vulnerable to any user who has compromised a client machine.
- The NFS server doesn’t recheck the client authentication on every request. The server assumes that if the client uses a valid file handle, the client is authorized to access that filesystem. An attacker with a forged or captured file handle can access the filesystem just as easily as a legitimate client can.
NFS Client Vulnerabilities
NFS clients may also be in danger from NFS servers. For example, an NFS-mounted filesystem may contain setuid programs; users on the client would be able to use those programs to become root. Device entries on an NFS-mounted partition are considered to apply to the client’s devices, not the server’s devices. Somebody with an account on an NFS client and root permission on an NFS server can use this to get unlimited, if inconvenient, read-write access to all data on the client.
Some NFS clients provide options to mount that can be used to disable devices and setuid/setgid on mounted filesystems. If mount is not available to users other than root, or if it always uses these options for users other than root, this will protect the client from the server.
If these options are not available, even if only root can mount filesystems, you should consider mounting an NFS filesystem to be equivalent to granting the server machine root access to the client.
Setting up a fixed port for mountd
gksudo gedit /etc/default/nfs-kernel-server
- comment out this line: RPCMOUNTDOPTS=–manage-gids
- add this instead: RPCMOUNTDOPTS=”–port 33333″
Or any other port number.
now try to reset nfs using:
sudo service nfs-kernel-server restart
And test if it helped using:
rpcinfo -p | grep "tcp.*mountd"
For me it wasn’t enough, but a full restart fixed the issue.
Setting up the firewall
(1) delete old rules, do this manually or reset if this is the only use for the firewall:
sudo ufw reset
sudo ufw enable
(2) add nfs & mountd ports
sudo ufw allow in from 10.0.0.1/20 to any port 111
sudo ufw allow in from 10.0.0.1/20 to any port 2049
sudo ufw allow in from 10.0.0.1/20 to any port 33333
(Change to your local IP’s or to “any” instead of 10.0.0.1/20)
So, that’s all in this blog. I will meet you soon with next stuff .Have a nice day !!!
Recommended contents
How to Check the Active Directory Database Integrity
Disabling and Enabling the Outbound Replication
DFS Replication Service Stopped Replication
What is Strict Replication Consistency
The replication operation failed because of a schema mismatch between the servers involved
Troubleshooting ad replication error 8418 the replication operation failed because of a schema mismatch between the servers
How to export replication information in txt file
Repadmin Replsummary
Enabling the outbound replication
Disabling and enabling replication on schema master domain controller
How to enable strict replication consistency
How to prevent lingering objects replication in active directory
AD replication process overview
How to force active directory replication
Change notification in replication process
How to check replication partner for a specific domain controller
dcdiag test replications
Guys please don’t forget to like and share the post.Also join our WindowsTechno Community and where you can post your queries/doubts and our experts will address them .
You can also share the feedback on below windows techno email id.
If you have any questions feel free to contact us on admin@windowstechno.com also follow us on facebook@windowstechno to get updates about new blog posts.