SMB Port
What is SMB
The Server Message Block Protocol (SMB Protocol) is a client-server communication protocol that is used on a network to share access to files, printers, serial ports, and data. It can also carry transaction protocols for inter-process communication that is authenticated.
In a nutshell, the SMB protocol allows computers to communicate with one another.
SMB Port
Server Message Block is a communication protocol originally developed in 1983 by Barry A. Feigenbaum at IBM and intended to provide shared access to files and printers across nodes on a network of systems running IBM’s OS/2. It also provides an authenticated inter-process communication mechanism.
SMB is a network file and resource sharing protocol that uses a client-server model that means where clients request a file, and the server provides it to the client.
Port 445 is used by Microsoft Directory Services for Active Directory (AD) and for the Server Message Block (SMB) protocol over TCP/IP.
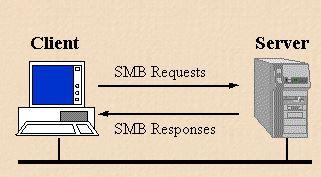
Client-server, request-response protocol called SMB. The operation of SMB is shown in the diagram on the left. SMB is a request-response protocol, so the only time it deviates from this rule is when a client requests opportunistic locks (oplocks) and the server later needs to break an oplock that has already been granted because another client requested a file open in a mode that is incompatible with the granted oplock. In this scenario, the server notifies the client of the oplock breach through an unsolicited message.
Clients on the network can access file systems and other resources like printers, mail slots, named pipes, and APIs thanks to servers. The hard drives on client PCs may be independent.
Is SMB secure?
Is SMB secure and safe to use? For the time being, it seems that way. New vulnerabilities, however, might surface at any time. If you’re not using any apps that require SMB to protect your system from potential dangers, it’s best to disable it entirely.
Because SMB is not enabled by default in Windows 10 as of October 2017, you only need to take action if you’re using an earlier version of Windows. The following activities are necessary to keep your SMB port secure:
SMB ports should not be exposed.
It has not been safe to open ports 135 through 139 and 445 for over a decade. Although opening ports 139 and 445 to the Internet is not inherently dangerous, there are several known drawbacks.
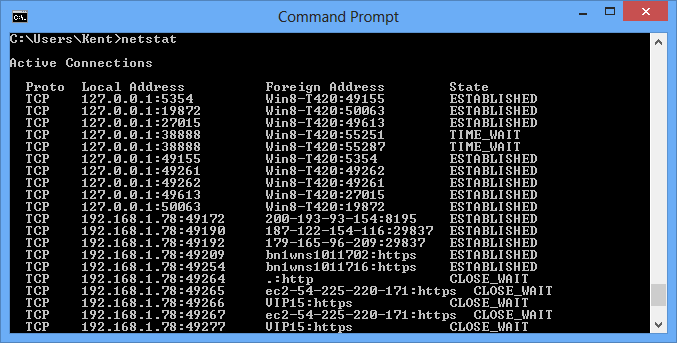
You may use the netstat command to see if a port is open.
How to Prevent SMB Vulnerabilities
The greatest prevention against an SMB attack is to patch your system. Attackers will be unable to get access to a patched PC, yet many Windows computers remain unpatched. Microsoft’s March 2017 update can help repair the server message block vulnerabilities. Using this repair is one of the most effective ways to protect a system.
The update patches are already included into Windows 10 and newer systems. As a result, the majority of SMB attacks target Windows 7 and earlier. Additionally, the WannaCry patch can protect against EternalBlue exploits and other similar flaws. These are some of the most effective SMB server security improvements available.
Finally, vulnerability scanning and managed detection and response services may help in the prevention and detection of SMB and other cyberattacks.
So, that’s all in this blog. I will meet you soon with next stuff .Have a nice day !!!
Recommended contents
How to Check the Active Directory Database Integrity
Disabling and Enabling the Outbound Replication
DFS Replication Service Stopped Replication
What is Strict Replication Consistency
The replication operation failed because of a schema mismatch between the servers involved
Troubleshooting ad replication error 8418 the replication operation failed because of a schema mismatch between the servers
How to export replication information in txt file
Repadmin Replsummary
Enabling the outbound replication
Disabling and enabling replication on schema master domain controller
How to enable strict replication consistency
How to prevent lingering objects replication in active directory
AD replication process overview
How to force active directory replication
Change notification in replication process
How to check replication partner for a specific domain controller
dcdiag test replications
Guys please don’t forget to like and share the post.Also join our WindowsTechno Community and where you can post your queries/doubts and our experts will address them .
You can also share the feedback on below windows techno email id.
If you have any questions feel free to contact us on admin@windowstechno.com also follow us on facebook@windowstechno to get updates about new blog posts.