What is LAPS Password Attribute
Hello All,
Hope this post finds you in good health and spirit.
This post is regarding Local Administrator Password Solution (LAPS).
LAPS Password Attribute

Microsoft’s LAPS is a useful tool for automatically managing Windows computer local Administrator passwords. LAPS stores the password for each computer’s local administrator account in Active Directory, secured in a confidential attribute in the computer’s corresponding Active Directory object.LAPS helps to reduce the workload and help local administrator or desktop team to manage local administrator password in active directory for a number of machines.
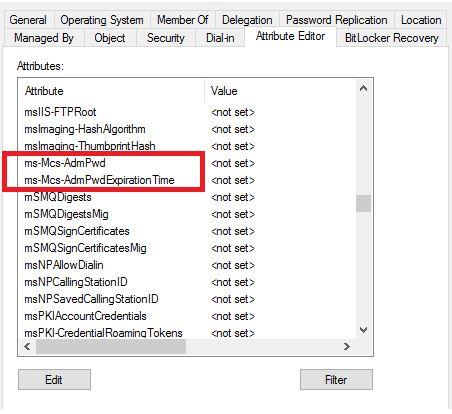
ms-mcs-AdmPwd
ms-mcs-AdmPwd – Its confidential computer attribute that stores the clear-text LAPS password.
It can only be viewed by Domain Admins by default, other ones can not view the respective object password and unlike other attributes, is not accessible by Authenticated Users. This value is blank until the LAPS password is changed.
For this security reason, delegation of the ms-mcs-AdmPwd attribute has to be carefully planned and performed and also do not replicate this attribute to RODC domain controller. Please see this article to exclude the confidential attribute from RODC replication.
ms-Mcs-AdmPwdExpirationTime
ms-Mcs-AdmPwdExpirationTime – This attribute stores the password expiration time.
This value is blank until the LAPS password is changed. When the LAPS password is changed, the value in this attribute automatically updated based on the LAPS password change threshold which is configured in the LAPS Group policy.
How does LAPS work ?
Microsoft’s LAPS is a useful tool for automatically managing Windows computer local Administrator passwords. LAPS stores the password for each computer’s local administrator account in Active Directory, secured in a confidential attribute in the computer’s corresponding Active Directory object.
LAPS helps to reduce the workload and help local administrator or desktop team to manage local administrator password in active directory for a number of machines.
- The core of the LAPS solution is a GPO client-side extension (CSE) that performs the following tasks and can enforce the following actions during a GPO update:
- Checks whether the password of the local Administrator account has expired.
- Generates a new password when the old password is either expired or is required to be changed prior to expiration.
- Validates the new password against the password policy.
- Reports the password to Active Directory, storing it with a confidential attribute with the computer account in Active Directory.
- Reports the next expiration time for the password to Active Directory, storing it with an attribute with the computer account in Active Directory.
- Changes the password of the Administrator account.
- The password then can be read from Active Directory by users who are allowed to do so. Eligible users can request a password change for a computer.
LAPS Prerequisites
Microsoft’s LAPS is a useful tool for automatically managing Windows computer local Administrator passwords. LAPS stores the password for each computer’s local administrator account in Active Directory, secured in a confidential attribute in the computer’s corresponding Active Directory object.
LAPS helps to reduce the workload and help local administrator or desktop team to manage local administrator password in active directory for a number of machines.
We need to confirm the following before we go ahead with the Microsoft LAPS configuration.
- Supported Operating System Windows Server 2019, Windows Server 2008, Windows Server 2016, Windows 10, Windows Server 2012 R2, Windows Server 2003, Windows Server 2008 R2, Windows Server 2012, Windows 7, Windows 8, Windows Vista, Windows 8.1, Windows Server 2022
Active Directory: (requires AD schema extension)
• Windows 2003 SP1 or later.
Managed machines:
• Windows Server 2003 SP2 or later, or Windows Server 2003 x64 Edition SP2 or later.
Note: Itanium-based machines are not supported.
Management tools:
• .NET Framework 4.0
• PowerShell 2.0 or later
LAPS Architecture
Microsoft’s LAPS is a useful tool for automatically managing Windows computer local Administrator passwords. LAPS stores the password for each computer’s local administrator account in Active Directory, secured in a confidential attribute in the computer’s corresponding Active Directory object.
LAPS helps to reduce the workload and help local administrator or desktop team to manage local administrator password in active directory for a number of machines.
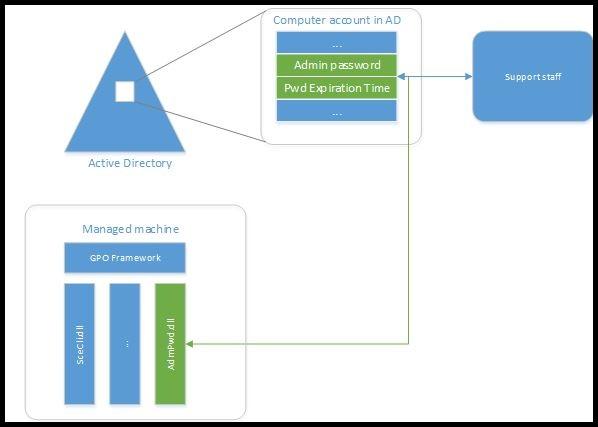
Core of the solution is GPO Client side Extension (CSE) that performs the following tasks during GPO update:
- Checks whether the password of local Administrator account has expired or not
- Generates the new password when old password expired or is required to be changed prior to expiration
- Changes the password of Administrator account
- Reports the password to password Active Directory, storing it in confidential attribute with computer account in AD
- Reports the next expiration time to Active Directory, storing it in confidential attribute with computer account in AD
- Password then can be read from AD by users who are allowed to do so
- Password can be forced to be changed by eligible users
So, that’s all in this blog. I will meet you soon with some other stuff. Have a nice day !!!
Recommended contents
RODC Installation Guide- Step by step guide to install read only domain controller
RODC Filtered Attribute Set
Installing and configuring a RODC in Windows Server-2012
How to find the GUID of Domain Controller
Group Policy Understanding Group Policy Preferences
Group Policy Verification Tool GPOTool Exe
Group Policy Health Check on Specific Domain Controller
What is Netlogon Folder in Active Directory
How to Create Custom Attributes in Active Directory
How Can I Check the Tombstone Lifetime of My Active Directory Forest
How to Determine a Computers AD Site From the Command Line
How to Check the Active Directory Database Integrity
How to Check the Active Directory Database Integrity
Disabling and Enabling the Outbound Replication
DFS Replication Service Stopped Replication
What is Strict Replication Consistency
The replication operation failed because of a schema mismatch between the servers involved
Troubleshooting ad replication error 8418 the replication operation failed because of a schema mismatch between the servers
How to export replication information in txt file
Repadmin Replsummary
Enabling the outbound replication
Guys please don’t forget to like and share the post.Also join our WindowsTechno Community and where you can post your queries/doubts and our experts will address them .
You can also share the feedback on below windows techno email id.
If you have any questions feel free to contact us on admin@windowstechno.com also follow us on facebook@windowstechno to get updates about new blog posts.
