Understanding SASE – The Convergence of Security and Networking
Unlike traditional network hardware and security point solutions, SASE is delivered primarily as a service. That means there are constant updates that enterprises must consider. These include new versions of a Cloud Access Security Broker (CASB), Zero Trust Network Access (ZTNA), secure gateway, or firewall. The benefits of a SASE solution are significant. It reduces risk and improves crisis management.
Identity-Based Zero Trust Network Access
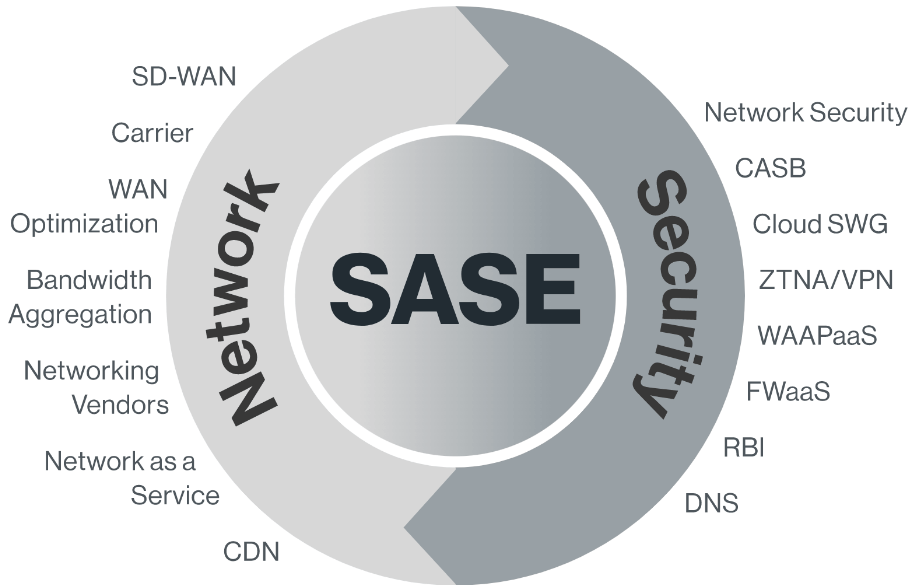
What is SASE? SASE (Secure Access Service Edge) is a cloud-based security framework that provides secure access to network resources from anywhere. Security services converge with networking at the edge of your network, which means you can stop attackers before they have a foothold in the corporate network. SASE integrates SD-WAN with network security functions like cloud access security brokers (CASB), secure web gateways (SWG), and firewall as a service to create a single, integrated platform for all networks – whether in the data center, branch office, mobile devices or public/private clouds.
This converged architecture at the network edge delivers typical cloud enhancements such as elasticity, flexibility, agility, and delegated management. The key to unlocking the total value of SASE is identity-driven security. This means that every connection to the enterprise network – including WAN connections, IoT devices, APIs, and serverless applications – is secured by the framework, with real-time context such as the user’s identity, location, risk/trust posture of the connecting device and application and data sensitivity determining which security services are applied.
An essential prerequisite to implementing SASE is identifying which of your existing point security and networking tools are no longer working at peak performance or have been rendered obsolete by new threats. This can help you plan a phased transition to a SASE framework, starting with adopting Zero Trust Network Access technologies and then building up your integrated security and networking capabilities portfolio.
Traffic Inspection
To realize the full benefits of SASE, all networking and security capabilities need to be offered as a unified service by the same provider. Attempting to bundle networking and security solutions from multiple vendors or relying on network chaining isn’t true convergence and can lead to complexity, a lack of control, and inefficient use of resources.
The ideal SASE solution provides:
- A single management console.
- A unified policy engine to streamline operations and increase effectiveness for network and security teams.
By reducing the number of tools that must be managed, these teams can focus on more challenging issues requiring the latest threat information.
A centralized view of security and networking data can help organizations spot threats hiding in siloed systems. By combining these functions, organizations can reduce their total cost of ownership. A unified SASE solution can deliver numerous benefits, including reducing costs and IT complexity, supporting remote access for mobile employees, enabling new digital business scenarios, and improving the user experience by routing traffic with latency optimizations and a global edge network.
To get started, organizations should conduct an assessment to identify their pain points and opportunities for improvement. This should include assessing network performance, security gaps, and remote access requirements. Then, a complete network design can be built with SASE in mind to solve these challenges and improve the organization’s overall security.
SD-WAN
As digital organizations break down traditional tech siloes and eliminate outdated technologies like VPNs, the need for a new approach to network security becomes apparent. SASE delivers on the promise of unified networking and security capabilities rolled into a single service from a vendor. This reduces costs, IT complexity, and the number of devices and agents installed at branch offices, remote locations, or end-user devices.
SASE uses a cloud-based architecture that combines networking and security functions in an application-driven model. Traffic is inspected and encrypted at distributed points of presence (PoPs) worldwide. This global network architecture enables low latency regardless of where users, branches, or IoT devices are located. Organizations should develop a roadmap for implementation to use SASE best. Ideally, this should include identifying key business goals and how SASE can support them.
This will help them select a provider with the right mix of services to meet their needs, such as reducing costs and IT complexity, enabling secure access for remote workers, delivering consistent policies across all users, and enhancing network performance. A centralized approach to security and networking can also reduce time spent on deployment, configuration, and ongoing maintenance chores.
Security Analytics
As cyber-attacks become more sophisticated and complex, the old methods of relying on rules, signatures, and patterns to detect them are no longer effective. That’s where security analytics comes in—to take the massive amounts of data generated by every device on a network and turn it into actionable information to minimize risk, respond quickly, and prevent attacks from ever occurring. A sophisticated security analytics platform can also provide proactive visibility into the entire ecosystem of a business, improve the employee experience, and drive better business outcomes.
It aggregates data from multiple sources, including SIEM systems and security as a service (SECaaS) providers. By bringing together the data, advanced features like machine learning and artificial intelligence enable the detection of anomalies, suspicious user behavior, insider threats, and other vulnerabilities that traditional tools cannot see. Security convergence is not just a technology solution—it requires a new way of working between networking and cybersecurity teams.
This means regular communication and a shared goal of stopping threats that threaten the business. Until these cultural barriers are removed, cybersecurity and networking teams will continue to work in separate siloes—with the result being that each team will miss critical threats and risks. The convergence of these two teams is necessary for business growth and success in the digital age.