Delegate permissions to Promote Domain Controllers
Hello all,
Hope this post finds you in good health and spirit.
This post is regarding how we can promote domain controller without domain admin rights. it can be done by low level delegations.
In this article, we will explain how to delegate permissions for a user/group to allow them promoting new Domain Controllers without adding them to Domain Admins or Enterprise Admins. Why i am looking this because i want to have two dedicated teams in active directory service.
The reason is having two different teams. One is doing high level AD tasks and the other manages routine things. The first one is using Domain Admin access. The second one is a normal administrative group that gets the delegated permissions for each task they do. Promoting DCs task is now being transferred to the second team .

Pre-requisite task
Before you start this, these are the pre-tasks need to action before you can DCpromo with Non-domain admin rights.
Logon to domain controller via domain admin credentials.
We are logon to DC via Mark-DS-A domain admin account as we have to perform some required task before achieve it .
Once logon to domain controller, please open the active directory users and computers console(DSA.msc).
Please create the one security group for domain controllers promotion.
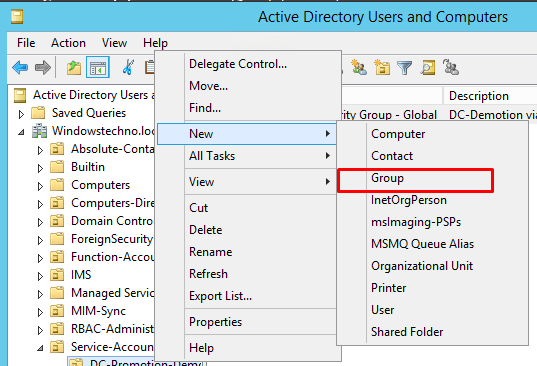
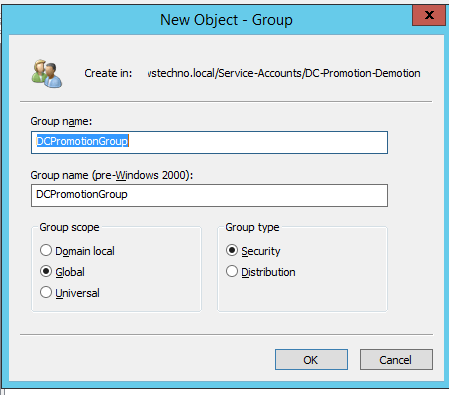
We are creating DCpromotionGroup and set the group scope as global and group type as security.
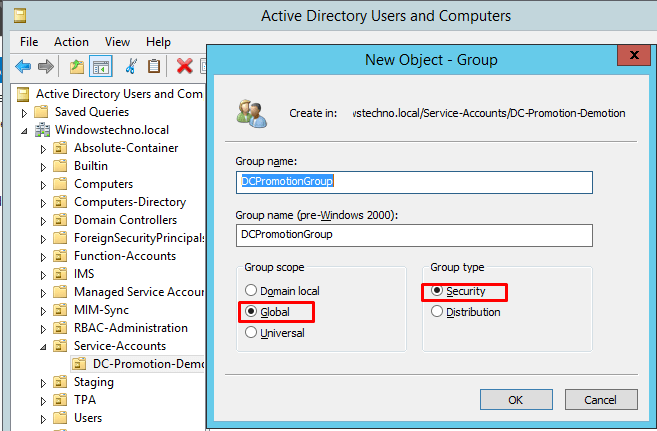
Click on OK.
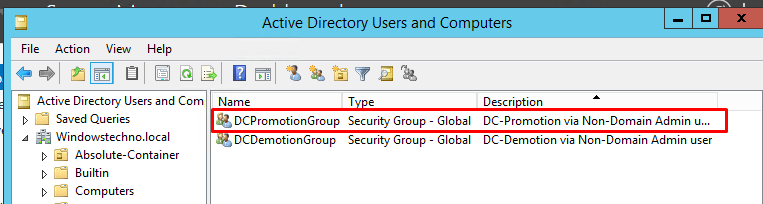
Now you can see the DCpromotionGroup group is created as per screenshot.
Now we have to add the Mike-DS-A account to DCpromotionGroup as we will promote domain controller via this account.This account has Non-domain admin rights.
Click on members
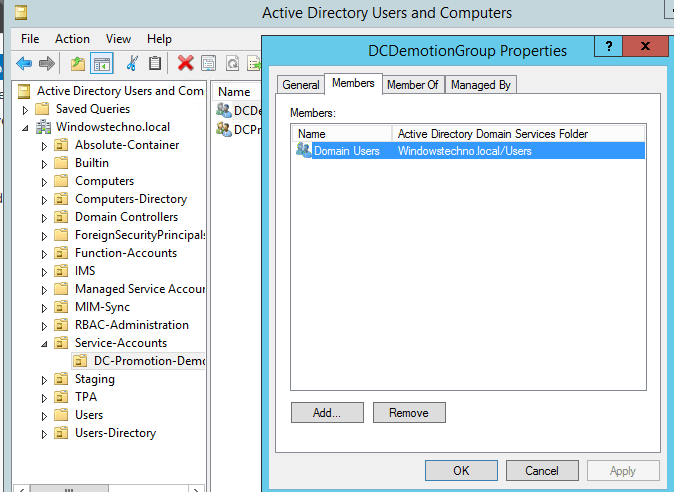
Add Mike-DS-A account to DCpromotionGroup.
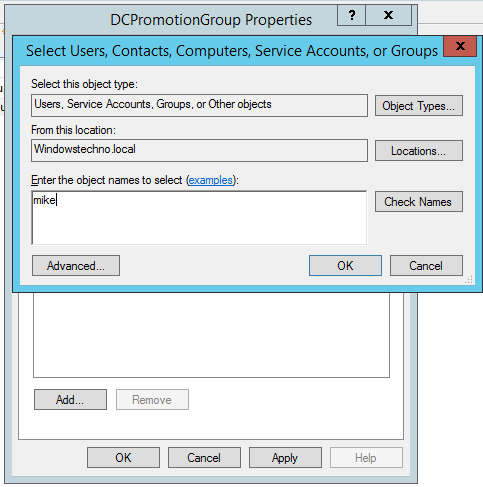
Click on check names
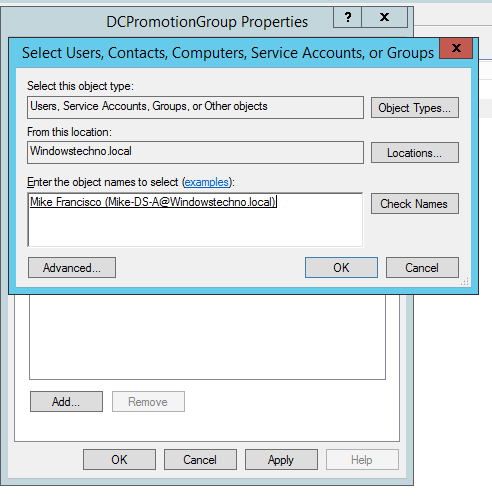
Click on OK and Apply.
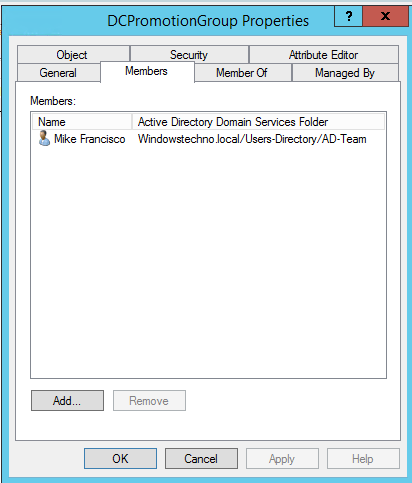
Now Mike-DS-A account is added to DCpromotionGroup group.
Come to Scripting part.
In larger enterprise deployments there is often the requirement to automate the building and promotion of domain controllers and their hardware. Such deployments utilize service accounts for different tasks. This document describes how to delegate the ability to promote a domain controller using the minimum required permissions. The idea being that a group is granted these permissions and the service account that performs the automated promotions is the only member of this group.
To delegate the ability to add a DC to an existing domain several permissions are required on several different containers. The following table lists the permissions required.
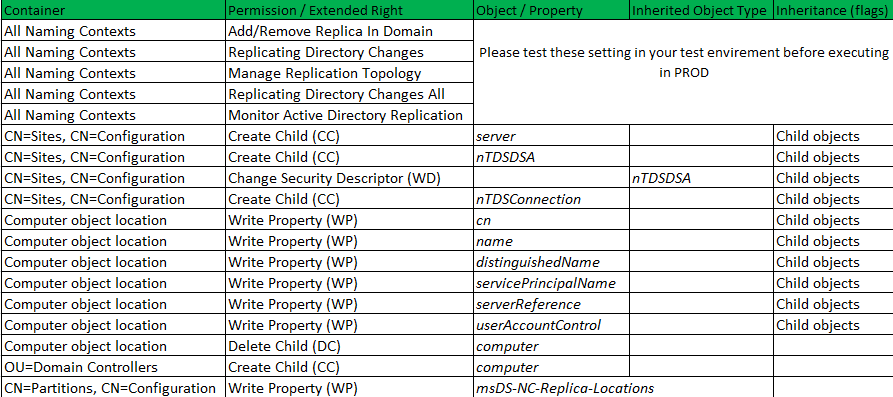
Minimum permissions required for promotion
Note. WP for msDS-NC-Replica-Locations isn’t strictly necessary, but is required if the service account will later wish to configure a DC to replicate a naming context, e.g. a new application partition.
There is two ways to configure these several permissions on several different containers. We can do it manually or via script. For manually doing this ,efforts will more and there can chance for mistake. So we go through via script.
The following script, AD-Man-DomJoinPerms.cmd configures these permissions. The script has two dependencies:
- ADFIND
- DSACLS
Note. ADFIND is a freeware tool available from www.joeware.net; DSACLS is a Windows Support Tool.
These applications need to either be in a folder that is defined within the path variable, or in the same current directory as the script is run from.We have copied both tools along with delegation script to C:\Windows\system32 folder.The script takes two arguments:
- The security principal (trustee) to grant the permissions to (preferably a group object)
- The distinguished name of the domain that you wish to delegate these permissions in, e.g. dc=domain-name,dc=com
Both sets of arguments must be enclosed in quotes, and the order is required.
Example: granting the group Add DCs the necessary permissions in the Windows Techno domain.
Listing: AD-Man-DomJoinPerms.cmd
:: Script sets the necessary permissions in the domain passed as an
:: argument (1) for the trustee passed as an argument (0) so that
:: that trustee can add domain controllers to the domain.
::
:: Script expects both ADFIND.EXE (V01.32.00cpp or higher) and
:: DSACLS.EXE to be present in the same directory as this script.
::
:: Example usage:
::
:: domjoinpermissions “TEST-LAB\Add domain controllers to the domain” “DC=test-lab,DC=com”
::
::
:: ** Note ** The script must be run from the CD of the script
:: location if ADFIND isn’t within the %PATH% otherwise
:: the script will fail with a “Cannot find ADFIND error”
::
:: ** Note ** Non-standard permissions are required to implement
:: this script. See accompanying documentation for
:: exact requirements.
::
::
:: Check that we have the correct arguments
if [%1]==[] (
GOTO :Usage
) else (
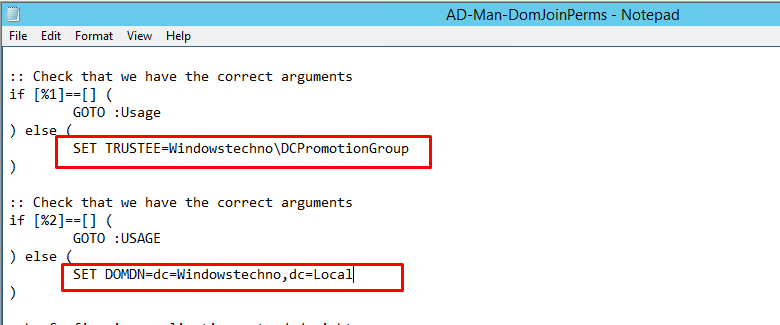
SET TRUSTEE=Windowstechno\DCPromotionGroup
):: Check that we have the correct arguments
if [%2]==[] (
GOTO :USAGE
) else (
SET DOMDN=dc=Windowstechno,dc=Local
)echo Configuring replication extended rights…
:: Set permissions on all local NCs
for /f “tokens=*” %%a in (‘adfind -b -s base namingContexts -list’) do (
echo/
echo [%%a]dsacls “%%a” /G %TRUSTEE%:CA;”Add/Remove Replica In Domain”;
dsacls “%%a” /G %TRUSTEE%:CA;”Replicating Directory Changes”;
dsacls “%%a” /G %TRUSTEE%:CA;”Manage Replication Topology”;
dsacls “%%a” /G %TRUSTEE%:CA;”Replicating Directory Changes All”;
dsacls “%%a” /G %TRUSTEE%:CA;”Monitor Active Directory Replication”;
)echo/
echo Configuring permissions on the sites container…:: Set the necessary permissions on the sites container
dsacls “CN=Sites, CN=Configuration,%DOMDN%” /G %TRUSTEE%:CC;server; /I:S
dsacls “CN=Sites, CN=Configuration,%DOMDN%” /G %TRUSTEE%:CC;nTDSDSA; /I:S
dsacls “CN=Sites, CN=Configuration,%DOMDN%” /G %TRUSTEE%:WD;;nTDSDSA /I:S
dsacls “CN=Sites, CN=Configuration,%DOMDN%” /G %TRUSTEE%:CC;nTDSConnection; /I:Secho/
echo Configuring permissions on the source (computers or staging, etc.) container…:: Set the necessary permission on the default computers container
:: NOTE. If REDIRCOMP has been run, %COMPCONT% must be changed to
:: reflect this.
SET COMPCONT=OU=Staging,%DOMDN%dsacls “%COMPCONT%” /G %TRUSTEE%:WP;cn;computer /I:S
dsacls “%COMPCONT%” /G %TRUSTEE%:WP;name;computer /I:S
dsacls “%COMPCONT%” /G %TRUSTEE%:WP;distinguishedName;computer /I:S
dsacls “%COMPCONT%” /G %TRUSTEE%:WP;servicePrincipalName;computer /I:S
dsacls “%COMPCONT%” /G %TRUSTEE%:WP;serverReference;computer /I:S
dsacls “%COMPCONT%” /G %TRUSTEE%:WP;userAccountControl;computer /I:S
dsacls “%COMPCONT%” /G %TRUSTEE%:DC;computer;echo/
echo Configuring permissions on the domain controllers OU…:: Set the necessary permissions on the domain controllers OU
dsacls “OU=Domain Controllers,%DOMDN%” /G %TRUSTEE%:CC;computer;:: Add permission to add NDNC replicas for SVC acct.
echo Granting WP for the msDS-NC-Replica-Locations attribute of the discoverer partitionfor /f “tokens=*” %%b in (‘adfind -configuration -rb CN=Partitions -f “nCName=DC=DiscovererPartition,%DOMDN%” -list distinguishedName’) do (
echo [%%b]dsacls %%b /G %TRUSTEE%:WP;msDS-NC-Replica-Locations;
)echo/
::Clean up
SET TRUSTEE=Windowstechno\DCPromotionGroup
SET DOMDN=DC=Windowstechno,DC=Local
SET COMPCONT=OU=Staging,%DOMDN%echo The application completed successfully
GOTO :EXIT
Above script will use to delegate the permissions to promote the domain controllers and we are using DCPromotionGroup group for domain controllers promotion.
Logon to domain controller via domain admin credentials.

We are login to DC with Mark-DS-A domain admin account as we have to delete permissions to DCPromotionGroup group to promote domain controllers without domain admin rights.

Go to My computer and open the C :\Windows\System32 folder as per below snapshot. Check script variables if you want see,otherwise we will execute the command .

Please open the command line console run as administrator as we are going to delegate the permissions as per script.
Click on yes.
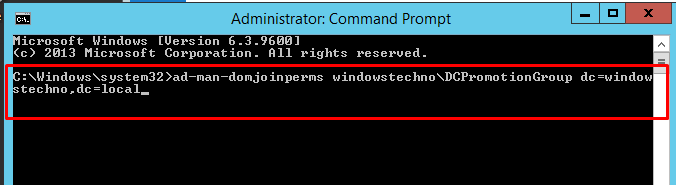
Kindly run this command
“ad-man-domjoinperms winowsTechno\DCPromotionGroup dc=WindowsTechno,dc=Local“
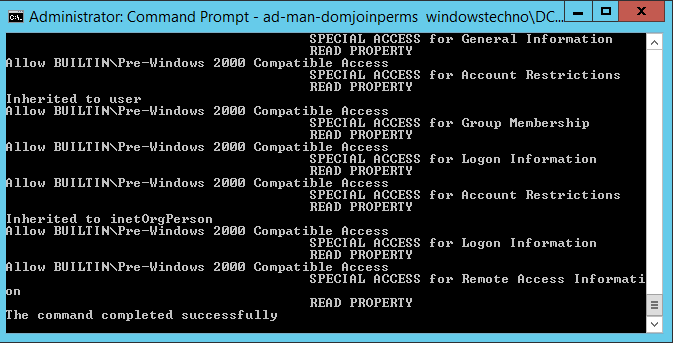
Once execute the above command , it start delegation the permissions as per script.
Delegation the permissions on several different containers
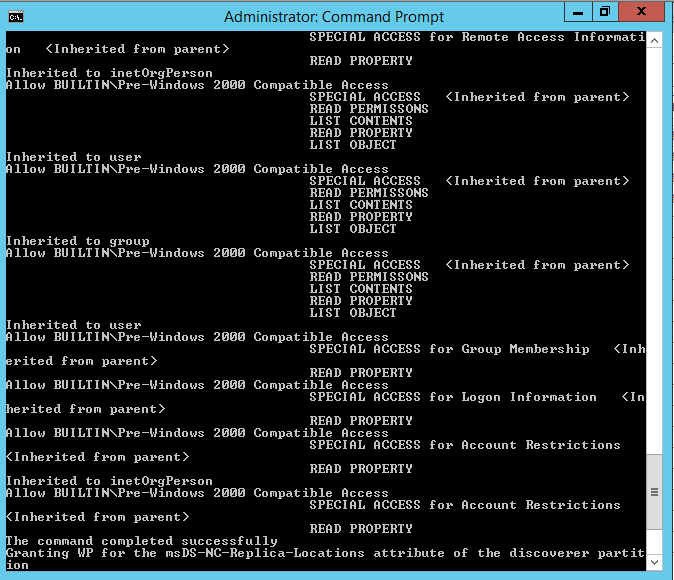
Kindly verify Once permissions are delegated on several different containers.Verify the permissions on Domain controllers OU.
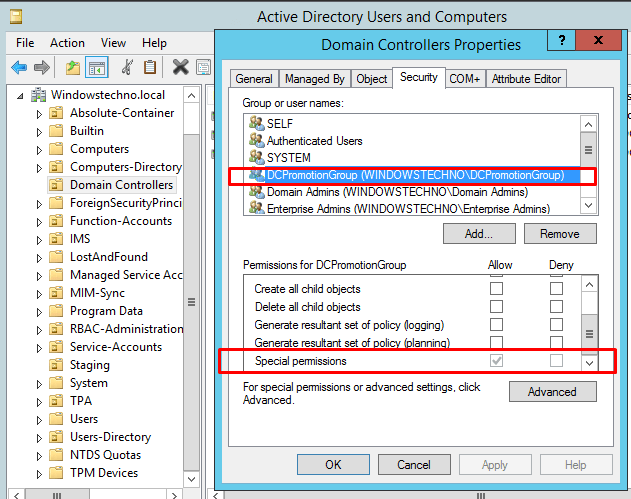
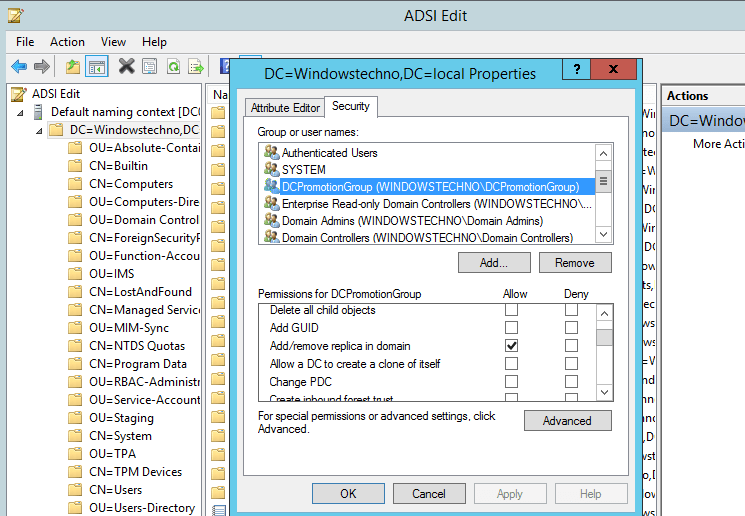
Verify the permission on default Naming context as per below screenshot.
Click on Property.
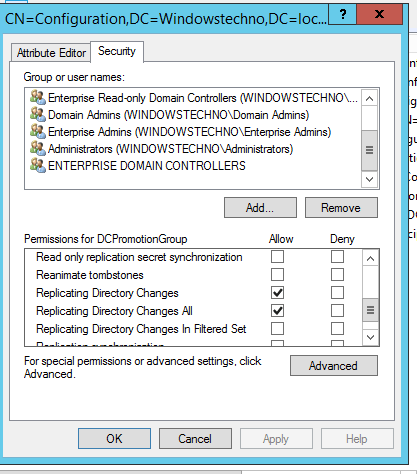
Verify the permission on configuration partition as per below screenshots.
Click on Security.
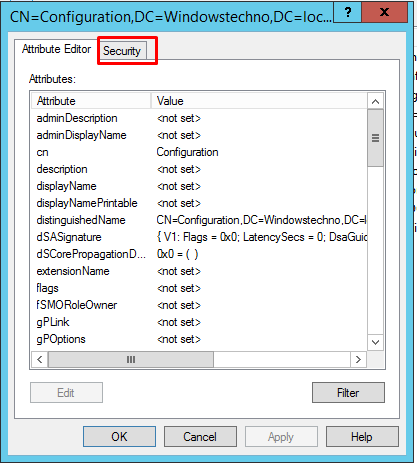
Verify the permissions.
Once verify the all the delegation permissions on several different containers , Logon to server which we want to promote as a domain controller without Non-domain Admin rights user.
Logon to server via domain admin credentials.
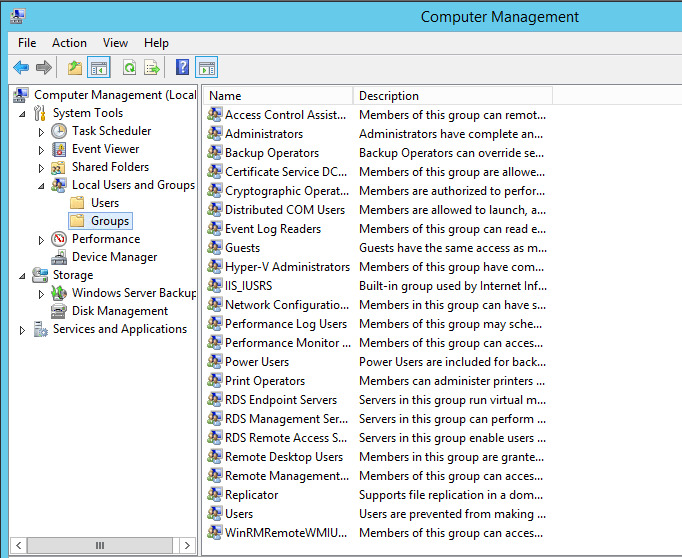
Open the computer management as we are going to add the DCPromotionGroup in administrators group of DC04 server.

Click on group container and click on administrator group as we will add DCpromotionGroup in local administrator group to grant the full access on DC04 server.
Click on Add
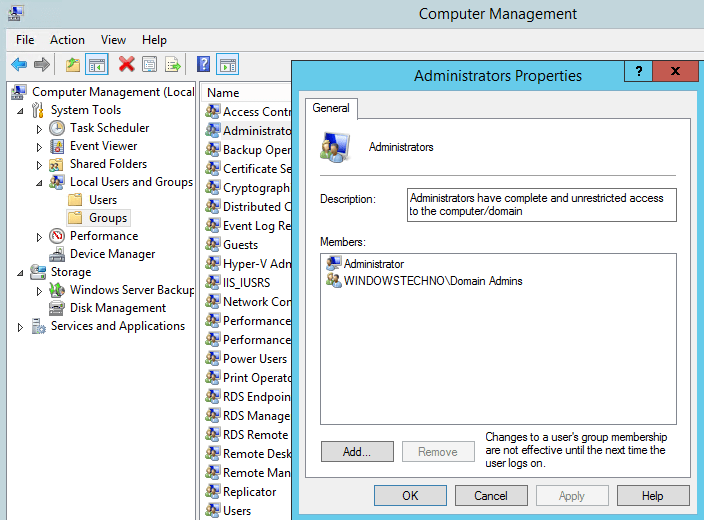
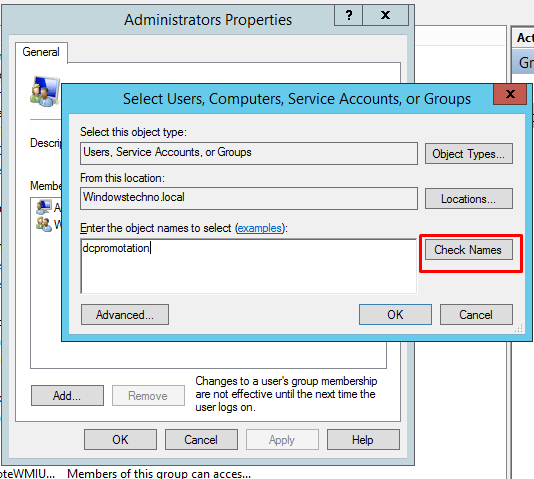
Add the DCPromotionGroup and click on check names.
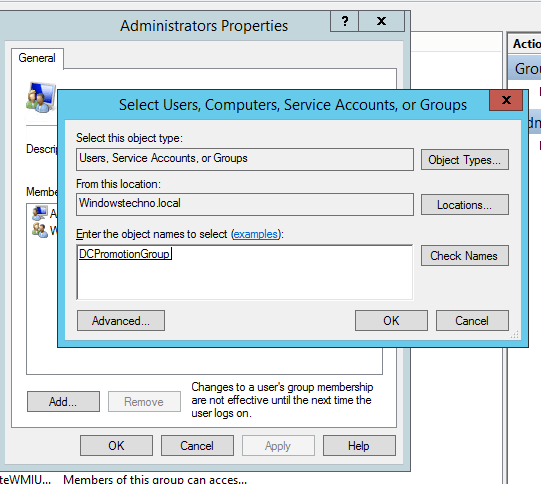
Click on OK
Apply and OK
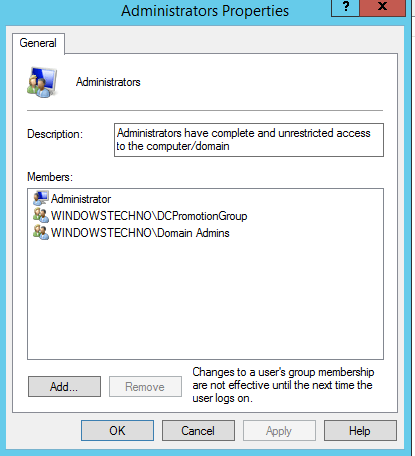
Kindly restart server once added the DCPromotionGroup in local administrator group of DC04 server.

Now Logon to server again via Mike-DS-A account as this account is added to DCpromotionGroup and required permissions are delegated to DCPromotionGroup on all required AD containers.
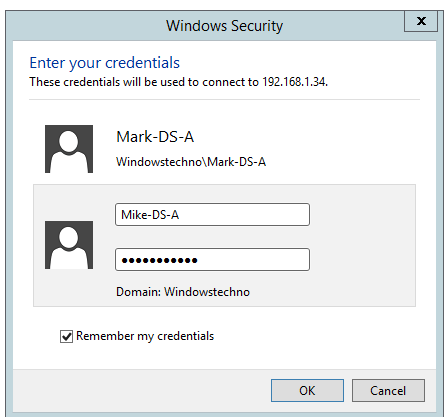
Kindly open the C drive to verify the Unattended answer file for promotion.

Open the command console run as administrator to execute the DC promotion command. As this time we are promoting domain controller by below command only instead of batch file.
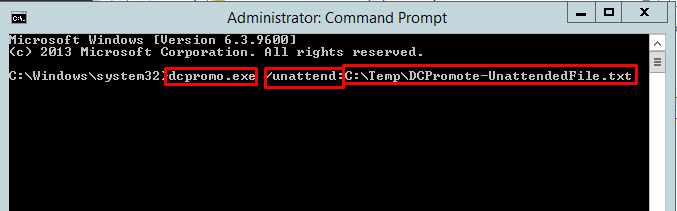
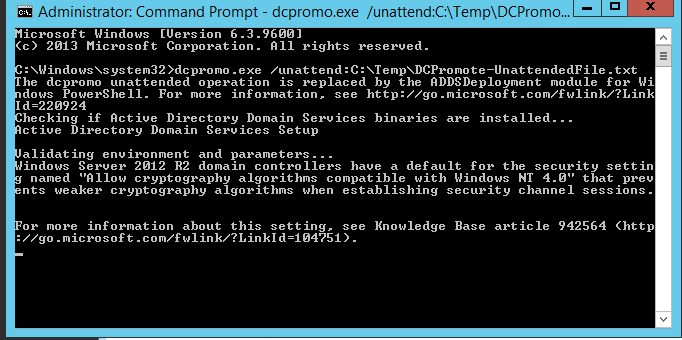
Execute the command.Now its checking the ADDS binaries are installed or not.
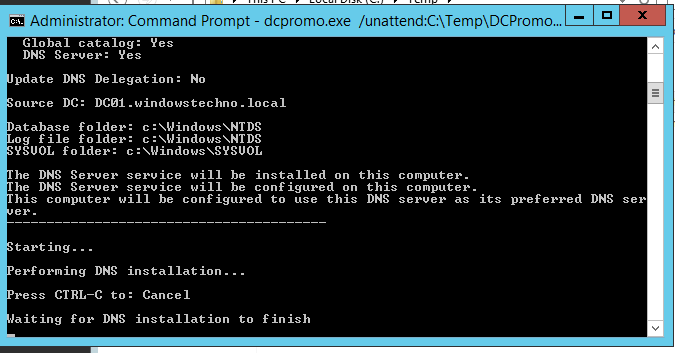
DNS installation
Group policy management console status.
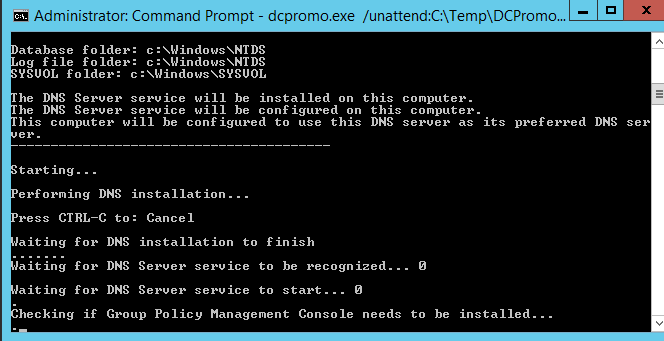
Replicating the configuration partitions.
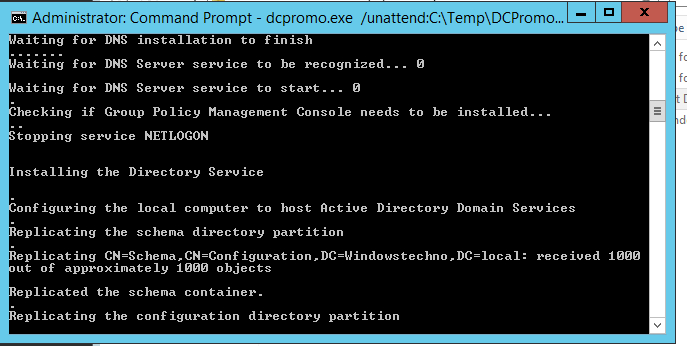
Replicating the critical domain information.
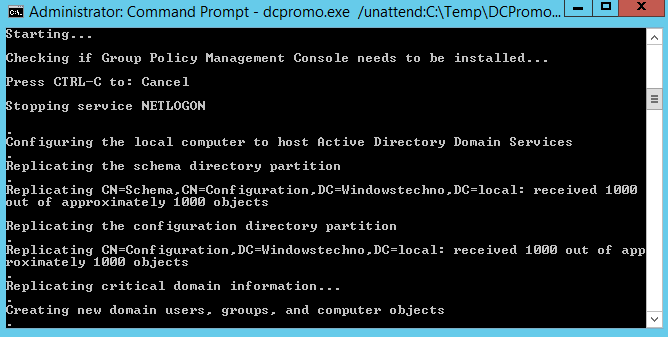
Active directory domain serveries is now installed on this computer as per below screenshot. Now we have installed the ADDS without having domain admin rights.
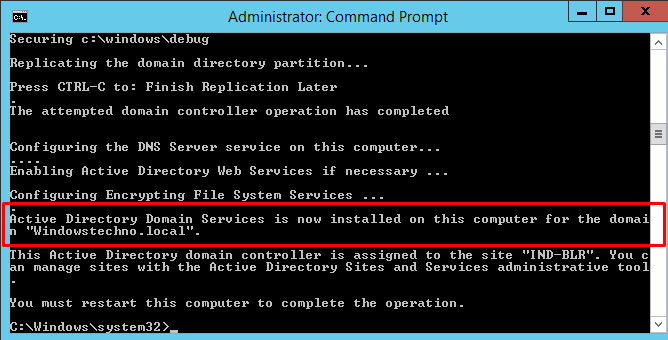
Restart the domain controller.
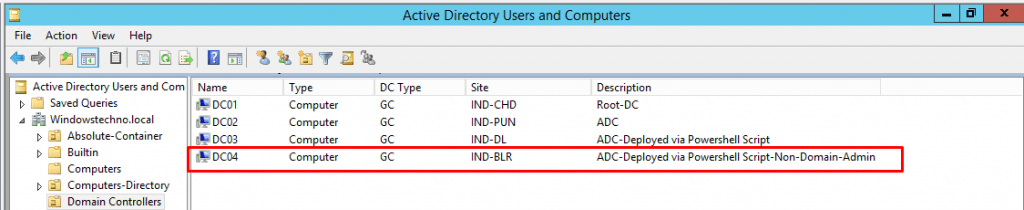
Logon to domain controller and verify the active directory domain services installation status.
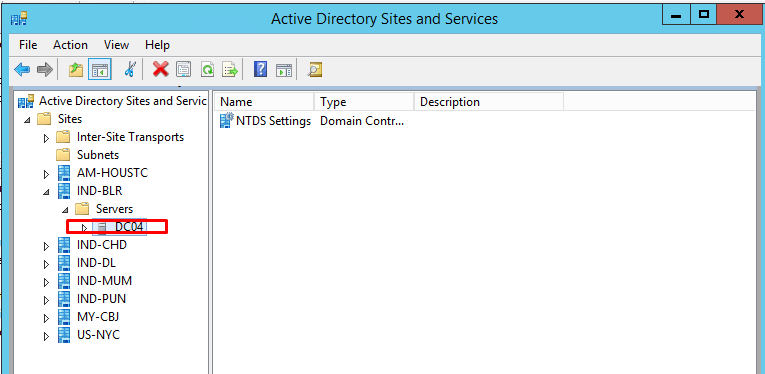
Verify from Active Directory Site and service console.
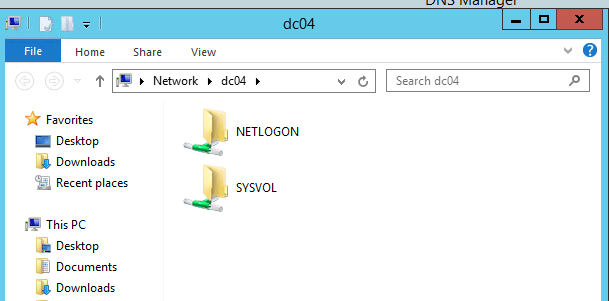
Verify sysvol and netlogon share
We live in such a special time when literally anything we can think of is possible.”
So, that’s all in this blog. I will meet you soon with next stuff .Have a nice day !!!
Recommended content
RODC Installation Guide- Step by step guide to install read only domain controller
RODC Filtered Attribute Set
Installing and configuring a RODC in Windows Server-2012
How to find the GUID of Domain Controller
Group Policy Understanding Group Policy Preferences
Group Policy Verification Tool GPOTool Exe
Group Policy Health Check on Specific Domain Controller
What is Netlogon Folder in Active Directory
How to Create Custom Attributes in Active Directory
How Can I Check the Tombstone Lifetime of My Active Directory Forest
How to Determine a Computers AD Site From the Command Line
How to Check the Active Directory Database Integrity
Guys please don’t forget to like and share the post.Also join our WindowsTechno Community and where you can post your queries/doubts and our experts will address them .
You can also share the feedback on below windows techno email id.
If you have any questions feel free to contact us on admin@windowstechno.com also follow us on facebook@windowstechno to get updates about new blog posts.

