How to update Active Directory Schema for LAPS
Hello All,
Hope this post finds you in good health and spirit.
This post is regarding How to update Active Directory Schema for LAPS- Local Administrator Password Solution .
Active Directory Schema for LAPS
Microsoft’s LAPS is a useful tool for automatically managing Windows computer local Administrator passwords. LAPS stores the password for each computer’s local administrator account in Active Directory, secured in a confidential attribute in the computer’s corresponding Active Directory object.

LAPS helps to reduce the workload and help local administrator or desktop team to manage local administrator password in active directory for a number of machines.
The Active Directory Schema needs to be extended to add two attributes to the computer class. These are ms-MCS-AdmPwd which stores the password in clear text, and ms-Mcs-AdmPwdExpirationTime which stores the password expiration time. You will need to be a member of the Schema Admins security group.
Microsoft LAPS uses two new attributes in computer objects.
ms-mcs-AdmPwd – Its confidential computer attribute that stores the clear-text LAPS password.
It can only be viewed by Domain Admins by default, other ones can not view the respective object password and unlike other attributes, is not accessible by Authenticated Users. This value is blank until the LAPS password is changed.
For this security reason, delegation of the ms-mcs-AdmPwd attribute has to be carefully planned and performed and also do not replicate this attribute to RODC domain controller. Please see this article to exclude the confidential attribute from RODC replication.
ms-Mcs-AdmPwdExpirationTime – This attribute stores the password expiration time.
This value is blank until the LAPS password is changed. When the LAPS password is changed, the value in this attribute automatically updated based on the LAPS password change threshold which is configured in the LAPS Group policy.
Schema changes are forest wide. Any changes done to the schema are handled by the schema master. There is only one schema master per forest. In other words, you should do it on the DC holding the schema master role. It is the role actually changing the schema. It will then replicate the changes to the other DCs. You will need to be member of schema admins and enterprise admins, domain admins.
Step-by-Step guide:How to extend the Schema for Microsoft Local Administrator Password Solution (LAPS)
- Login to Schema master role and disable the outbound replication before start the schema changes.Doing this we can stop the replicate changes to entire forest if in case of any issue comes.
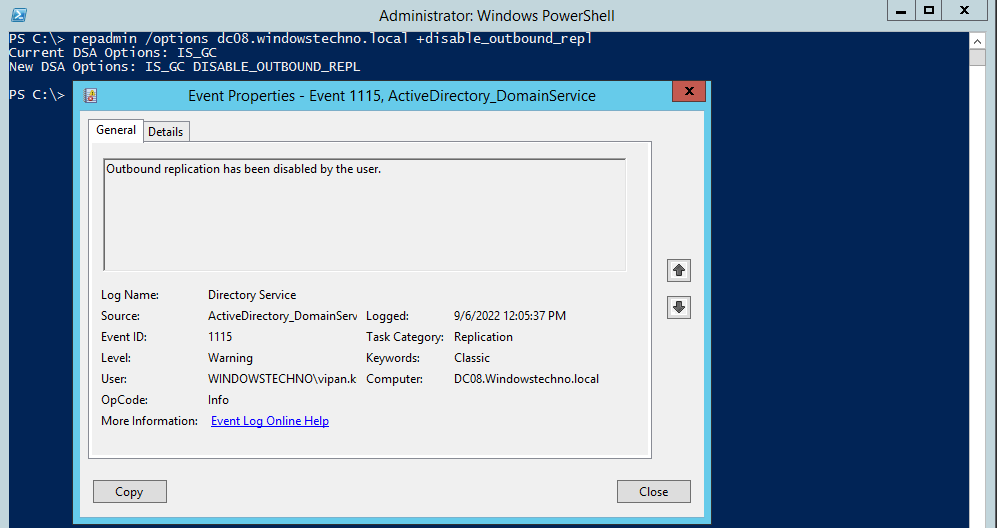
Please make sure Schema master is isolated and should be in separate AD site. Please open the Schema site change link and Change replication schedule from “Replication Available” to “Replication Not Available” for all timeframe.
1. Launch PowerShell as Active Directory Schema Administrator.
2. Then import PowerShell module using
Import-module AdmPwd.PS
3. Once the module is imported successfully, run Update-AdmPwdADSchema to update the schema.
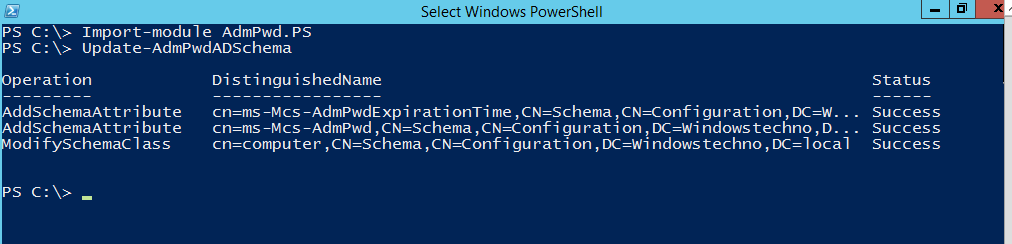
It introduces two new attributes to Active directory schema once we execute this command. These changes are non reversible that means these changes can not roll back , but yes we can un-map the attributes from respective class to remove these changes in front end.
Whenever we do any changes in system or respect to any services, all changes information registers in event viewer with timestamp.These Schema changes are triggered and registered in event viewer .
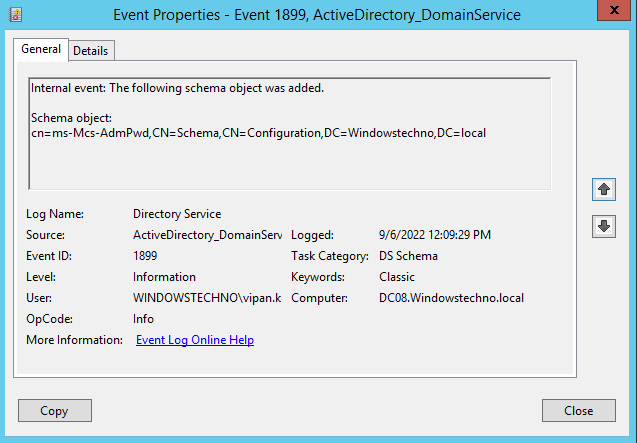
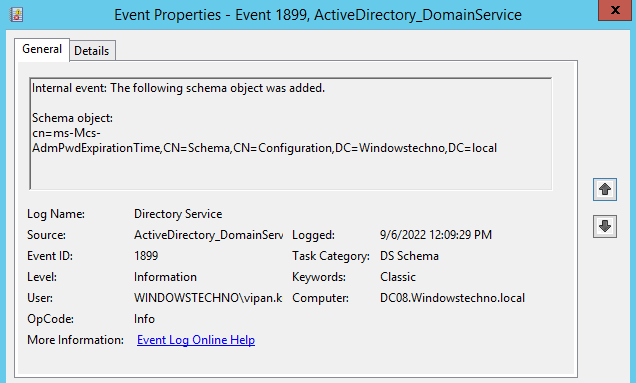
Two attributes added and mapped with computer class.
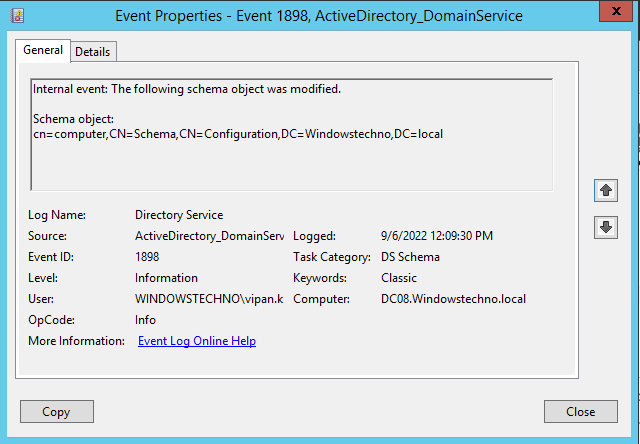
Please restart the ADDS service on schema master to reflect these attribute changes in computer object.
Open the services.msc and go to ADDS service
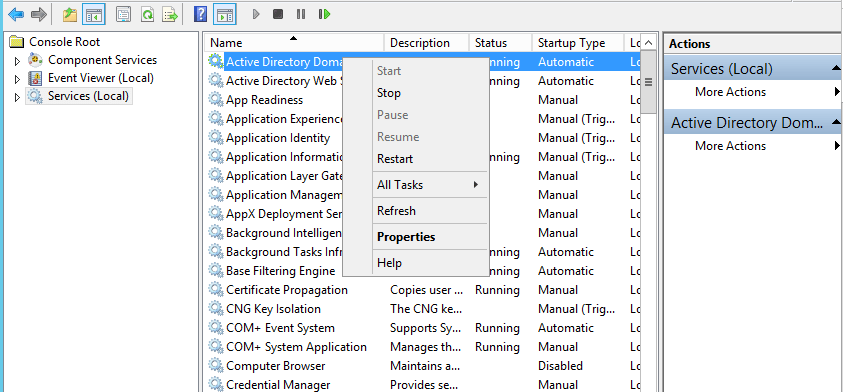
Click on restart as per below screenshot.
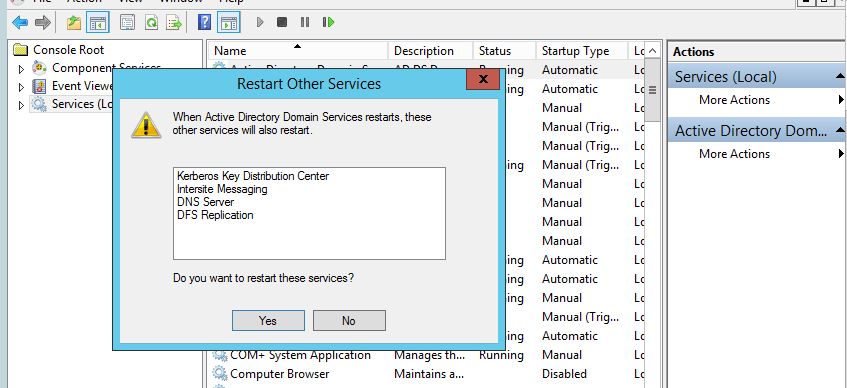
After service restarted, we can see these two new attributes in the computer object.
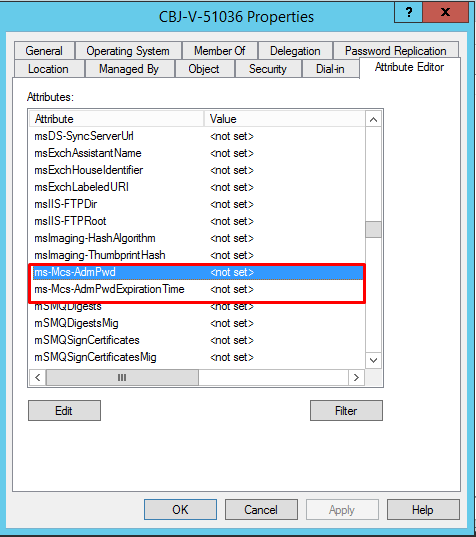
Initially , We disabled the outbound and site link replication to avoid any issue with schema but now schema changes are done and successfully tested and can enable outbound replication.
Please do not enable outbound replication until testing is completed and all things looks good respective to Schema.
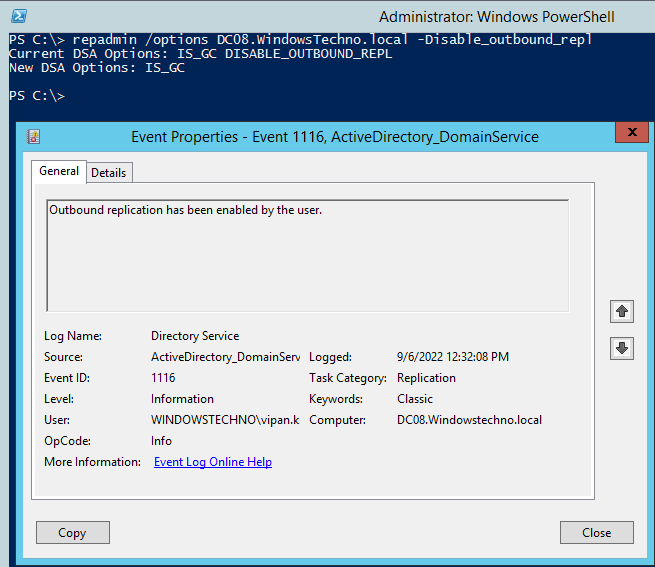
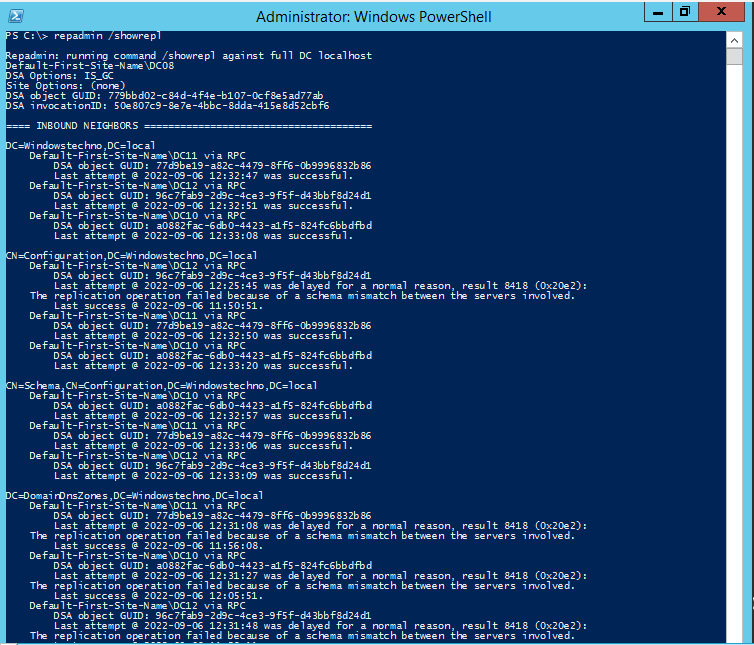
Wait for some time and check the replication as well schema changes to another domain DCs.
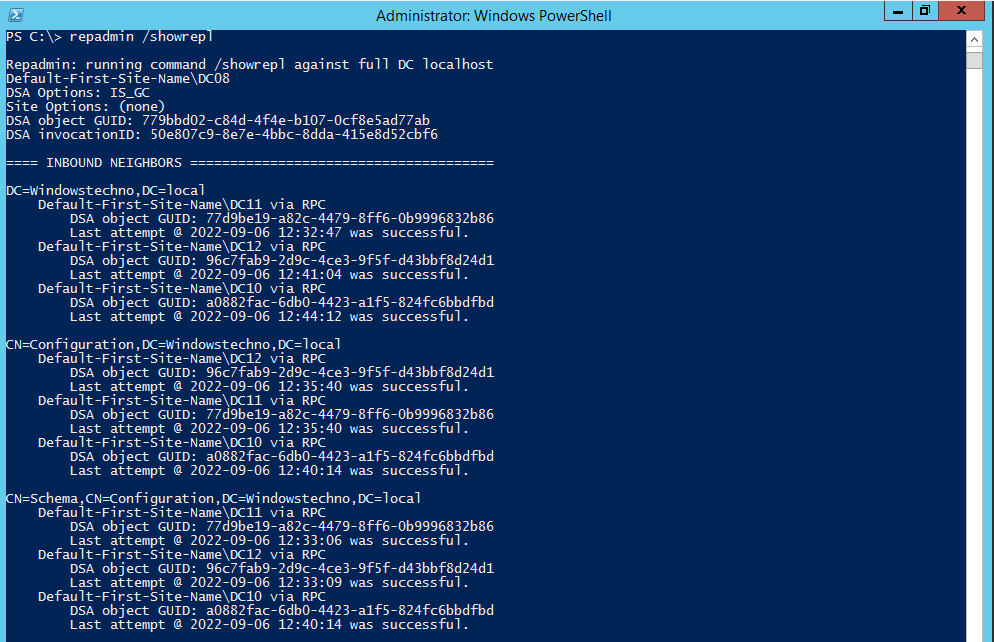
Now these changes are replicated to all DCs and this is how we introduced two attributes for LAPS-Local Administrator Password Solution.
So, that’s all in this blog. I will meet you soon with next stuff .Have a nice day !!!
Recommended contents
How to Check the Active Directory Database Integrity
Disabling and Enabling the Outbound Replication
DFS Replication Service Stopped Replication
What is Strict Replication Consistency
The replication operation failed because of a schema mismatch between the servers involved
Troubleshooting ad replication error 8418 the replication operation failed because of a schema mismatch between the servers
How to export replication information in txt file
Repadmin Replsummary
Enabling the outbound replication
Disabling and enabling replication on schema master domain controller
How to enable strict replication consistency
How to prevent lingering objects replication in active directory
AD replication process overview
How to force active directory replication
Change notification in replication process
How to check replication partner for a specific domain controller
dcdiag test replications
DFS Replication Event
Unidirectional replication
Guys please don’t forget to like and share the post. You can also share the feedback on below windows techno email id.
If you have any questions feel free to contact us on admin@windowstechno.com also follow us on facebook@windowstechno to get updates about new blog posts.
