Legacy applications are not working after installing the Jan 2023 patches
Hello All,
Hope this post finds you in good health and spirit.
2003 servers’ authentication is not working after installing the Jan 2023 patches.
Kerberos authentication is failing after installing the Jan 2023 patches. it has been detected and reported earlier in November and It seems that Microsoft have released already a fix, as documented in the Known Issues section of this rollup but again issue is detected in jan month patches.
Shared folder are not accessible
“Domain credentials are not working” error in Remote Desktop Connections
Error in Legacy application authentication.
Error: GSSException: Failure unspecified at API level (Mechanism level: AES256 CTS mode with HMAC SHA1-96 encryption type not in permitted_cnctypes list)
The November and Jan 2023 updates, according to MS “break Kerberos in situations where you have set the ‘This account supports Kerberos AES 256 bit encryption’ or ‘This account supports Kerberos AES 128 bit encryption’ Account Options set” (i.e., the msDS-SupportedEncryptionTypes attribute on user accounts in AD). Any Kerberos authentication situation inside impacted business setups can be impacted by the known problem, which Microsoft is currently investigating.
You can have Kerberos authentication problems on Windows Servers with the Domain Controller role after installing updates issued on November 8, 2022 or later. According to Microsoft. You can see a Microsoft-Windows-Kerberos-Key-Distribution-Center Event ID 14 error event in the System section of your Domain Controller’s Event Log with the following language when this problem arises.
The phrase “the missing key has an ID of 1” will be used to identify errors that are recorded in the system event logs of impacted systems. The account “account name” didn’t have an appropriate key for producing a Kerberos ticket while processing an AS request for the target service “service,” and the missing key has an ID of 1, according to the reported problems. The following examples of Kerberos authentication situations are just a few.
- Signing in as a domain user might fail. Authentication with Active Directory Federation Services (AD FS) may potentially be impacted by this.
- It’s possible for Group Managed Service Accounts (gMSA) to have authentication issues when used with services like Internet Information Services (IIS Web Server).
- Domain user remote desktop connections might not succeed.
- Shared folders on workstations and file shares on servers may not be accessible.
- Printing operations that need domain
There are many workaround to fix this problem. We will explain all the workaround those will help to resolve this problem but before that please understand the RC4 and AES 256 encryption. The main difference between AES and RC4 is that they use separate ciphers. AES is blocking encryption that uses block sizes to encode plain text. On the other hand, RC4 is a stream encryption algorithm that encrypts a bit at a time, similar to how a stream flows. Comparison Table Between AES and RC4
| Parameters | AES | RC4 |
| Meaning | The Advanced Encryption Standard is a type of symmetric block encryption. | Rivest Cipher 4 is a symmetric stream cipher. |
| Source | In 1997, an open contest was held to design AES. | In 1987, Ron Rivest created RC4. |
| Security | AES is a much more secure algorithm than RC4. | RC4 is much less safe than AES. |
| Key lengths | 128, 192, and 256 bits | 64 or 128 bits |
| Uses | SSL, TSL, etc. | NASA, NIST, etc |
Workaround
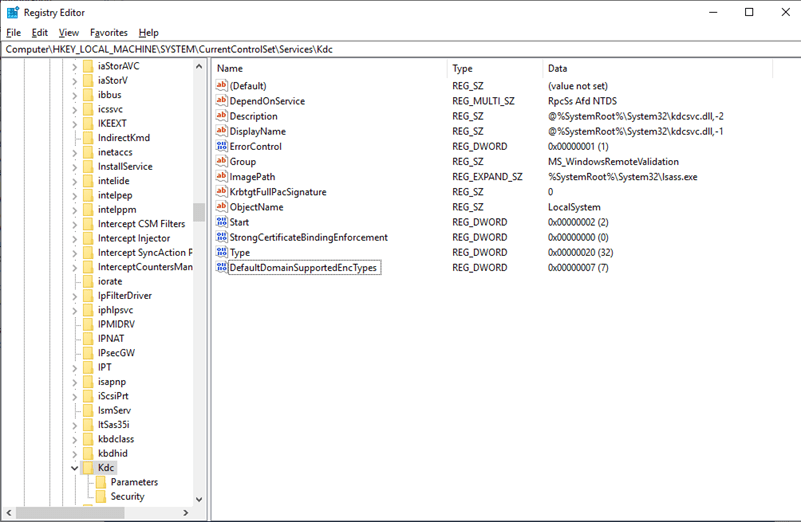
Please add the below registry entry on domain controllers to support RC4 protocol.
HKLM\SYSTEM\CurrentControlSet\Services\KDC\DefaultDomainSupportedEncTypes with a value of 0x7.
If you have multiple domain controllers in environment, please add this registry value via GPO instead making changes on all DCs manually. But please keep in mind this is temporary workaround and we should not place it as permanently. As we know RC4 encryption is insecure and vulnerable and we should not keep our domain controller as vulnerable. Also change the value of computer object in AD for the Windows Server 2003 file server msDS-SupportedEncryptionTypes attirbute a value of 4.
You can use the powershell command:
Set-ADComputer NameSERVERWithUnsupportedSO -Add @{'msDS-SupportedEncryptionTypes'=4}
Or
Set-ADComputer NameSERVERWithUnsupportedSO -Add @{'msDS-SupportedEncryptionTypes'=7} Important note- Please try to upgrade your existing Legacy applications to higher encryption so that your application can authenticate with domain controllers that are using AES 128 and AES 256 bit encryption.
So, that’s all in this blog. I will meet you soon with next stuff .Have a nice day !!!
Recommended content
How to Check the Active Directory Database Integrity
Disabling and Enabling the Outbound Replication
DFS Replication Service Stopped Replication
What is Strict Replication Consistency
The replication operation failed because of a schema mismatch between the servers involved
Troubleshooting ad replication error 8418 the replication operation failed because of a schema mismatch between the servers
How to export replication information in txt file
Repadmin Replsummary
Enabling the outbound replication
Disabling and enabling replication on schema master domain controller
How to enable strict replication consistency
How to prevent lingering objects replication in active directory
AD replication process overview
How to force active directory replication
Change notification in replication process
How to check replication partner for a specific domain controller
dcdiag test replications
Guys please don’t forget to like and share the post. You can also share the feedback on below windows techno email id.
If you have any questions feel free to contact us on admin@windowstechno.com also follow us on facebook@windowstechno to get updates about new blog posts.