What is Lateral Movement?
What is Lateral Movement?
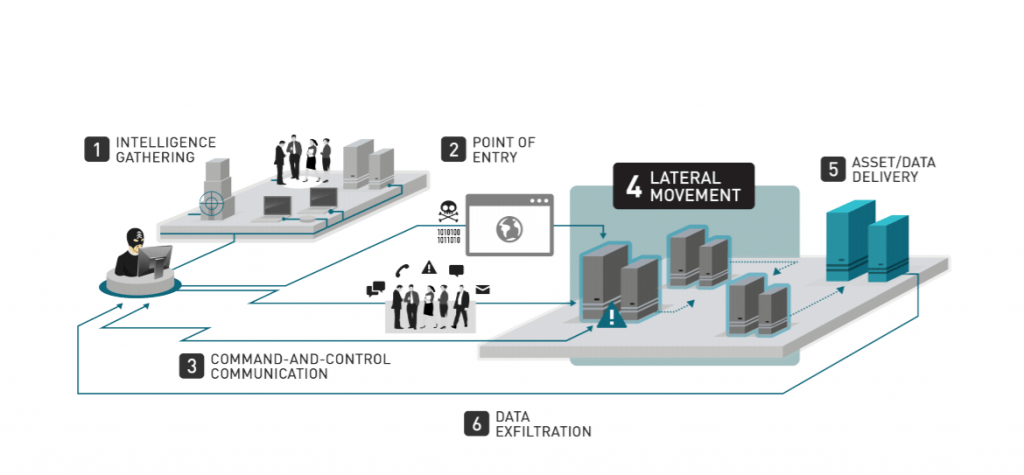
Lateral movement means to a technique used to identify, gain access to sensitive data. Lateral Movement consists of techniques that adversaries use to enter and control remote systems on a network and gain the access to your sensitive data and destroy it or publish on public platform.
The attacker will use different tools and methods to gain higher privileges and access, allowing them to move laterally (sideways; between devices and apps) through a network to map the system, identify targets and eventually get to the organization’s crown jewels. If the attacker is able to secure administrative privileges, malicious lateral movement activities can be extremely difficult to detect, as it can appear as “normal” network traffic to security pros who don’t have the skills to differentiate or are overwhelmed by a flurry of alerts.
IT administrators must also be knowledgeable on how their network infrastructure looks like at the baseline, which can be used as a point of comparison to help identify if the organization has been compromised. The presence of tools that have the same function. Moreover, a centralized location for all those who log in a system is a reliable way to detect any unauthorized access.and in every organization there should be a dedicated cyber defense team so that they can do the monitoring and configure some important rules alerts and review these alerts or logs everyday. I know, we do not review the logs until there is any cyber threat or any incident come in picture. So please do not make this practice and put monitoring on these all logs as well at network side.
There are two common ways by threat moves laterally. In the first approach, the attacker uses do internal scanning to find out what other machines are inside the network and also scan for open ports that are listening and machines that are suffering from vulnerabilities. At that point, the attacker can use these weaknesses to move laterally to another asset.
The second way for lateral movement exploits stolen credentials, and it is more common way. In this type of attack, the bad attacker might use a phishing email to infect a machine that interfaces with a particular server. The attacker can use his access to scrape for passwords via a keylogger or password-stealing tools like Mimikaz.
How we can prevent environment about these lateral movement??
Now this is the question how we can protect our environments from these threats.
Many high-profile attacks occurred over months of dwell time and moved laterally to easily evade standard security. attackers count on the fact that many organizations continue to rely on legacy or standard security solutions — the kind of technology that is easily bypassed by modern hacking tools. Now it’s very important to upgrade to technology that includes next-gen AV and behavioral analysis capabilities if you aim to combat today’s sophisticated attacks. Use an endpoint detection and response (EDR) tool to detect if someone launches malicious code on a protected IT asset.
Remove vulnerabilities such as outdated or unpatched systems and software that may be lurking in your network environment. Exploits can remain hidden for long periods of time before becoming active, and organizations will be exposed if they fail to apply patches and updates across all of their endpoints.
Use Local Administrator Password Solution” (LAPS) provides management of local account passwords of domain joined computers. Passwords are stored in Active Directory (AD) and protected by ACL, so only eligible users can read it or request its reset.
There are many Solutions to stop lateral movement in data breaches.You can find these solutions or steps on google. There are many articles are published by Cyber defense team. We will explain about active directory security in coming articles. These will be totally depend on active directory security, How we can protect active directory from these threats .
So, that’s all in this blog. I will meet you soon with some other stuff. Have a nice day !!!
Recommended content
RODC Installation Guide- Step by step guide to install read only domain controller
RODC Filtered Attribute Set
Installing and configuring a RODC in Windows Server-2012
How to find the GUID of Domain Controller
Group Policy Understanding Group Policy Preferences
Group Policy Verification Tool GPOTool Exe
Group Policy Health Check on Specific Domain Controller
What is Netlogon Folder in Active Directory
How to Create Custom Attributes in Active Directory
How Can I Check the Tombstone Lifetime of My Active Directory Forest
How to Determine a Computers AD Site From the Command Line
How to Check the Active Directory Database Integrity
How to Check the Active Directory Database Integrity
Disabling and Enabling the Outbound Replication
DFS Replication Service Stopped Replication
What is Strict Replication Consistency
The replication operation failed because of a schema mismatch between the servers involved
Troubleshooting ad replication error 8418 the replication operation failed because of a schema mismatch between the servers
How to export replication information in txt file
Repadmin Replsummary
Enabling the outbound replication
Guys please don’t forget to like and share the post. You can also share the feedback on below windows techno email id.
If you have any questions feel free to contact us on admin@windowstechno.com also follow us on facebook@windowstechno to get updates about new blog posts.

